-
Tenable
-
View All Histrory

資料處理中, 請稍候...
Loading...
Identities are the new perimeter — compromised identities are at the center of nearly every successful cyberattack.

Identities are the new perimeter — compromised identities are at the center of nearly every successful cyberattack. By uncovering misconfigurations, over-privileged access, and weaknesses in Active Directory (AD) and Entra ID, Tenable Identity Exposure strengthens your security posture and prevents identity-based attacks before they occur.
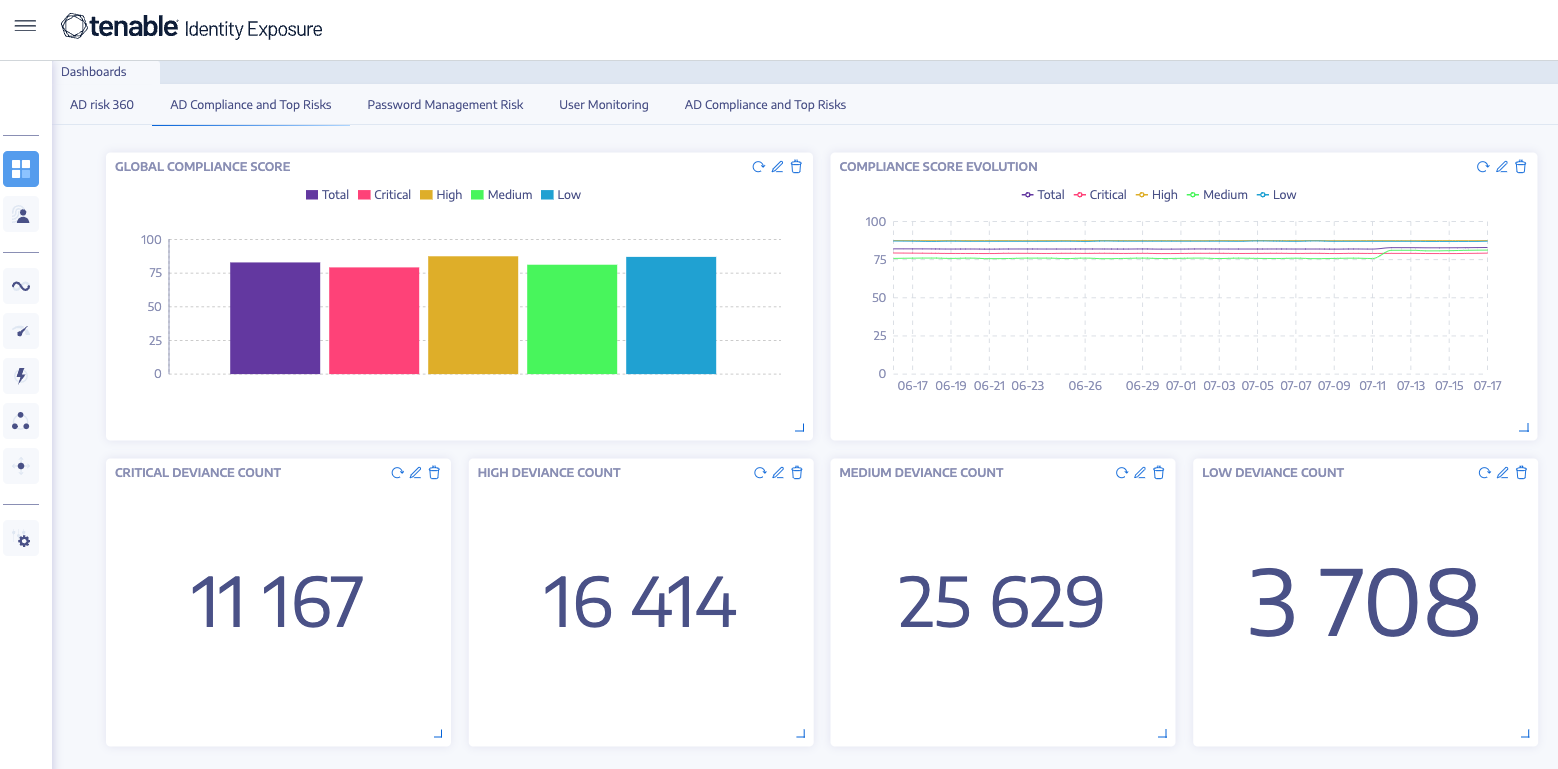
See the bigger pictureTenable Identity Exposure unifies and analyzes your identity risk surface, continuously validating AD and Entra ID for weaknesses, misconfigurations and risky permissions. Integrating deep identity context into the Tenable One Exposure Management Platform can help eliminate silos, uncover toxic combinations and prioritize risks, so you can remediate the exposures that matter most. | 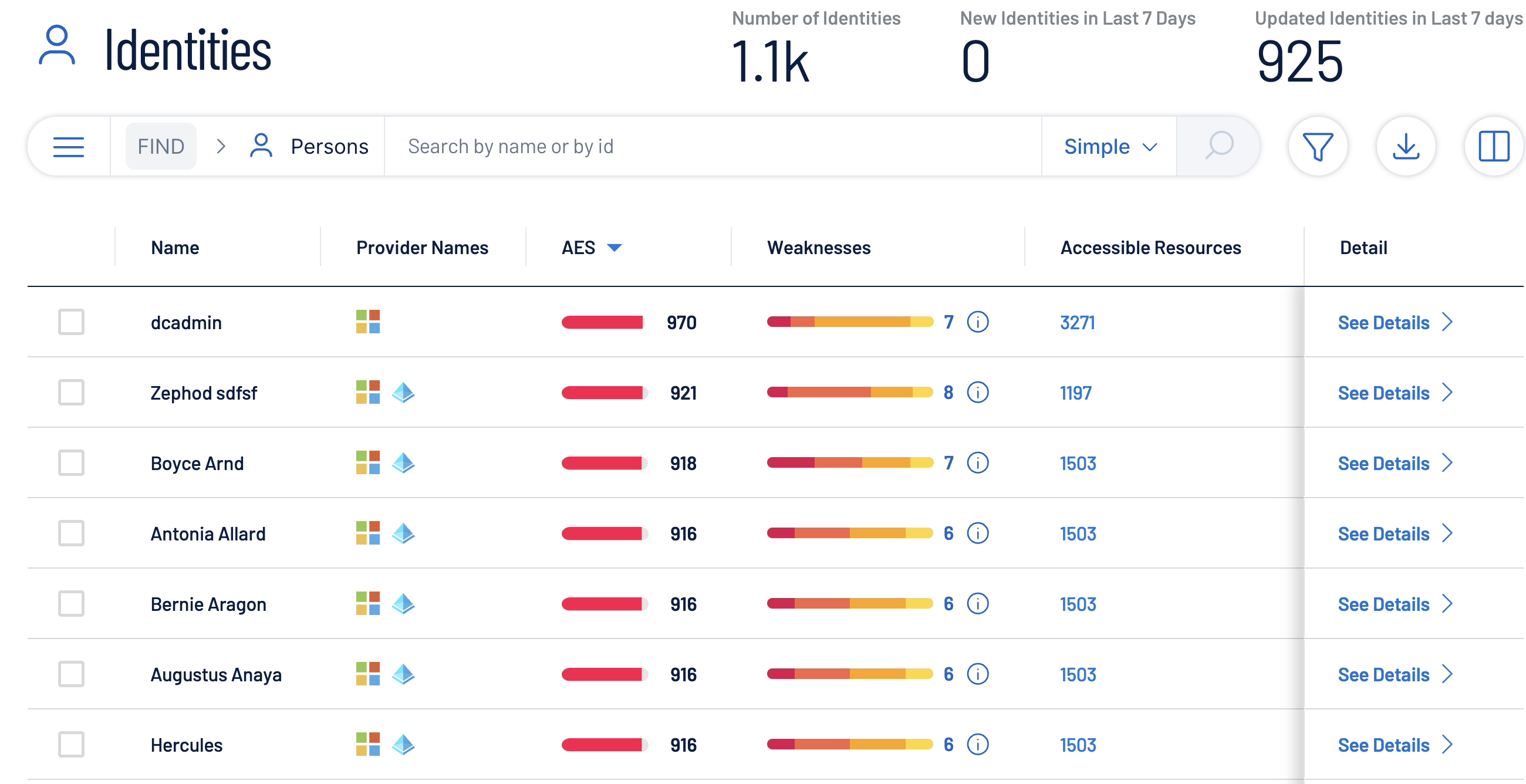 |
Tenable Identity Exposure eliminates the exposures and attack paths bad actors might otherwise exploit, ensuring attackers struggle to find a foothold and have no next step if they do.
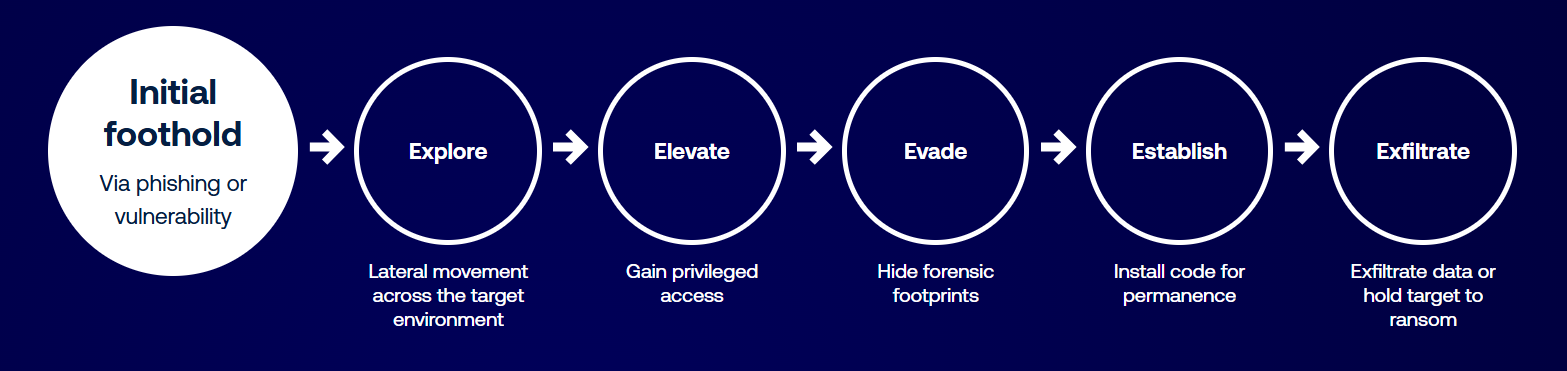
 | Secure hybrid identity infrastructure
|
 Deployed your waySecures Active Directory (AD) and Entra ID with flexible deployment options: On-prem for full control over your identity data, or SaaS for scalable cloud-based security. |  Secure without the riskTenable Identity Exposure is fully agentless, operating with just a standard user account to audit configurations and detect advanced identity threats in real time. |
 Customer Service Hotline
Customer Service Hotline
Customer service hours 9:00 - 18:00
 Customer Service Email
Customer Service Email
Send us your valuable feedback via E-mail