Loading...
資料處理中, 請稍候...
Loading...

Quantum Security Gate ways
Provides multi-layered network protection, including firewalls, intrusion prevention systems (IPS), etc. to prevent unauthorized access and external threats.
Select plan and quantity
Why Check Point AI-Powered, Cloud Delivered Threat Prevention is trusted by over 100,000 enterprises worldwide
Over 30 years leading security innovation has delivered the industry’s #1 block rate and defined the gold standard for security policy management.
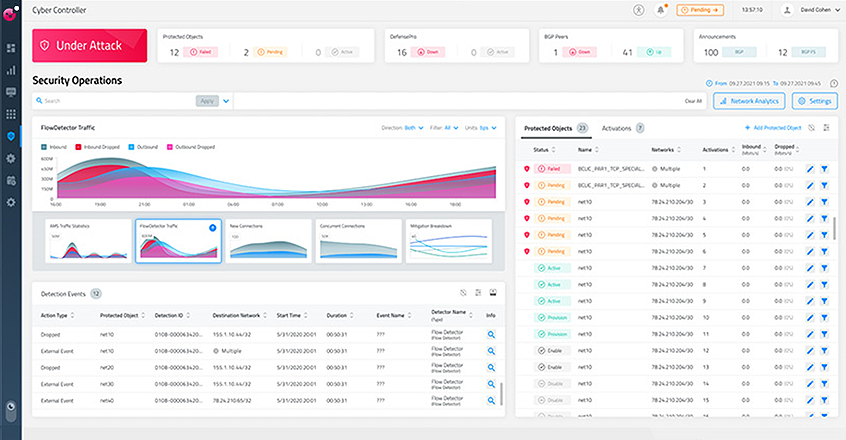 | One of the most important architectures in INIFITY is the latest generation, called QUANTUM Firewall (APT-level firewall). It has all our security functions and provides customers with powerful network security protection capabilities. There is no need to limit firewall capabilities for performance, and it can meet real security protection needs. By adjusting the performance of the hardware through self-developed software, functions can be enabled and performance can be effectively utilized. |
| Security scalability – Different devices can be combined to create secure gateway clusters based on different needs. Meet business growth and future needs - Best suited to the security needs of growing and start-up companies, greatly simplifying management and maintenance issues. Cloud Data Center-level Scalability – Telecom/cloud center-level security architecture, with performance and availability as you wish. | 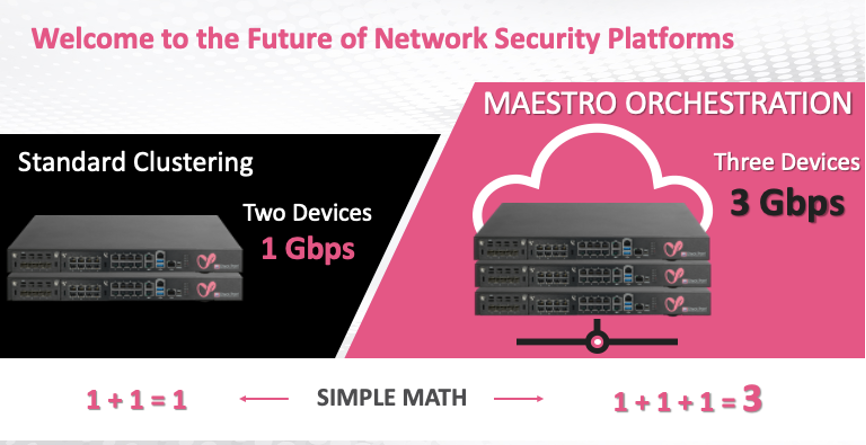 |
 | Advantages: To improve the traditional firewall which can only use Active-Standby architecture, Check Point has entered Active-Active-Active...clustered information security architecture. During periods of increased traffic, it only takes six minutes to add new equipment and put it into operation. The industry's highest defense performance is 1Tbps, and the maximum number of devices can reach 52. Effective average performance differentiation achieves a mechanism for uninterrupted service and continuous security defense. |

 還沒找到最適合的?
還沒找到最適合的?
別擔心,還有更多雲端工具等你探索
IScloud360 集合百款合法 SaaS,從人資到行銷、從財務到客服,總有一款能解決你的問題
前往館別總覽
Harmony Email Collaboration
Avanan is embedded directly within Micr...
Cloudflare Gateway
Cloudflare’s security portfolio is desig...

OSecure Email Filtering Service
OSecure integrates global threat intelli...

Defense Trust
A next-generation threat management plat...
-
0987654321
Service Hotline
Customer service hours 9:00 - 18:00
-
test111@iscom.com.tw
Contact Email
Send your valuable comments by E-mail
 Continue Shopping
Continue Shopping
 Once your order is complete, we'll send the order details to your email.
Once your order is complete, we'll send the order details to your email.
 Cart Details
Cart Details
 即時線上報價| 免等待立即登入試算
即時線上報價| 免等待立即登入試算
 Request for Quotation
Request for Quotation
