Loading...
資料處理中, 請稍候...
Loading...

EndBlock EDR
EndBlock captures all endpoint behavior, providing a full view of cyberattacks by tracing all compromised footprints and analyzing the hacker’s intrusion methods.
Select plan and quantity
Key to EndBlock’s Success
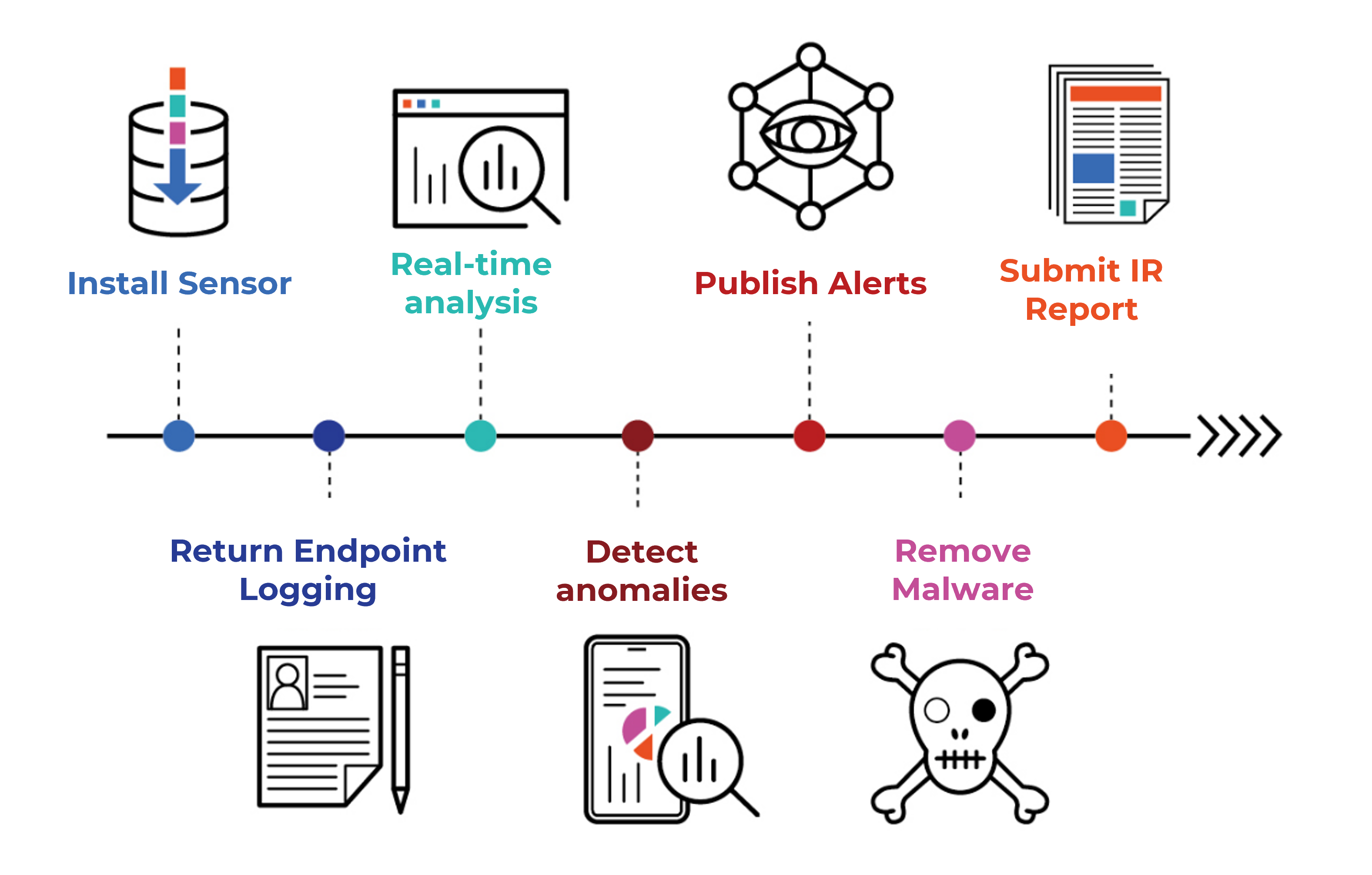
- A cybersecurity incident means that existing security devices have already been bypassed by attackers.
- Once these devices are bypassed, they no longer trigger alerts.
- As a result, organizations are unlikely to detect intrusions until significant damage has occurred.
- EndBlock automates traditional manual forensics, transforming it into a proactive and real-time analysis tool.
- Within minutes of a hacker breaching the system, EndBlock launches its investigation — minimizing the potential damage.
Service Workflow
 還沒找到最適合的?
還沒找到最適合的?
別擔心,還有更多雲端工具等你探索
IScloud360 集合百款合法 SaaS,從人資到行銷、從財務到客服,總有一款能解決你的問題
前往館別總覽
Harmony Endpoint
Endpoint security plays an increasingly ...

ITSec MDR Integration Platform
Integrate Microsoft Defender for Endpoin...
-
0987654321
Service Hotline
Customer service hours 9:00 - 18:00
-
test111@iscom.com.tw
Contact Email
Send your valuable comments by E-mail
 Continue Shopping
Continue Shopping
 Once your order is complete, we'll send the order details to your email.
Once your order is complete, we'll send the order details to your email.
 Cart Details
Cart Details
 即時線上報價| 免等待立即登入試算
即時線上報價| 免等待立即登入試算
 Request for Quotation
Request for Quotation
