資料處理中, 請稍候...
Loading...

Defense Trust
A next-generation threat management platform that integrates multiple security features to strengthen network perimeter protection.
Select plan and quantity
 | Defense Trust New Generation Threat ManagementOur solution offers the most comprehensive IP and DNS threat database, effectively neutralizing over 80% of known malicious websites, including phishing sites, malware downloads, botnets, and C&C connections. With the adoption of inline mode, Defense Trust ensures rapid comparison, minimal network latency, and precise inspection. Our intelligence database, updated daily, offers the industry’s fastest update rate, resulting in a nearly zero false alarm rate. Our fully automated system minimizes the need for maintenance personnel, and our built-in hardware and software bypass mechanism greatly reduced production downtime during power outages. |
Supports Integration with Standard Syslog Using CEF Format | |
New-Generation Defense CloudThe honeypot mechanism is for users to actively detect any potential threats or attacks from hackers through decoy setup. The deception technology mechanism focuses on proactively empowering users in establishing chaos network environment for misleading potential attackers' perception and decision-making process and letting Defense Cloud threat intelligence hunting system easily identify unknown attacks. | 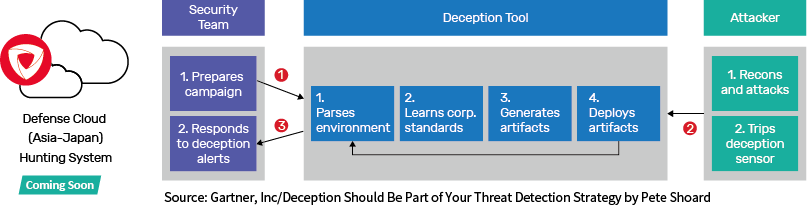 |
Global IP Analysis and Identification, Large-scale Known Malicious IPs | 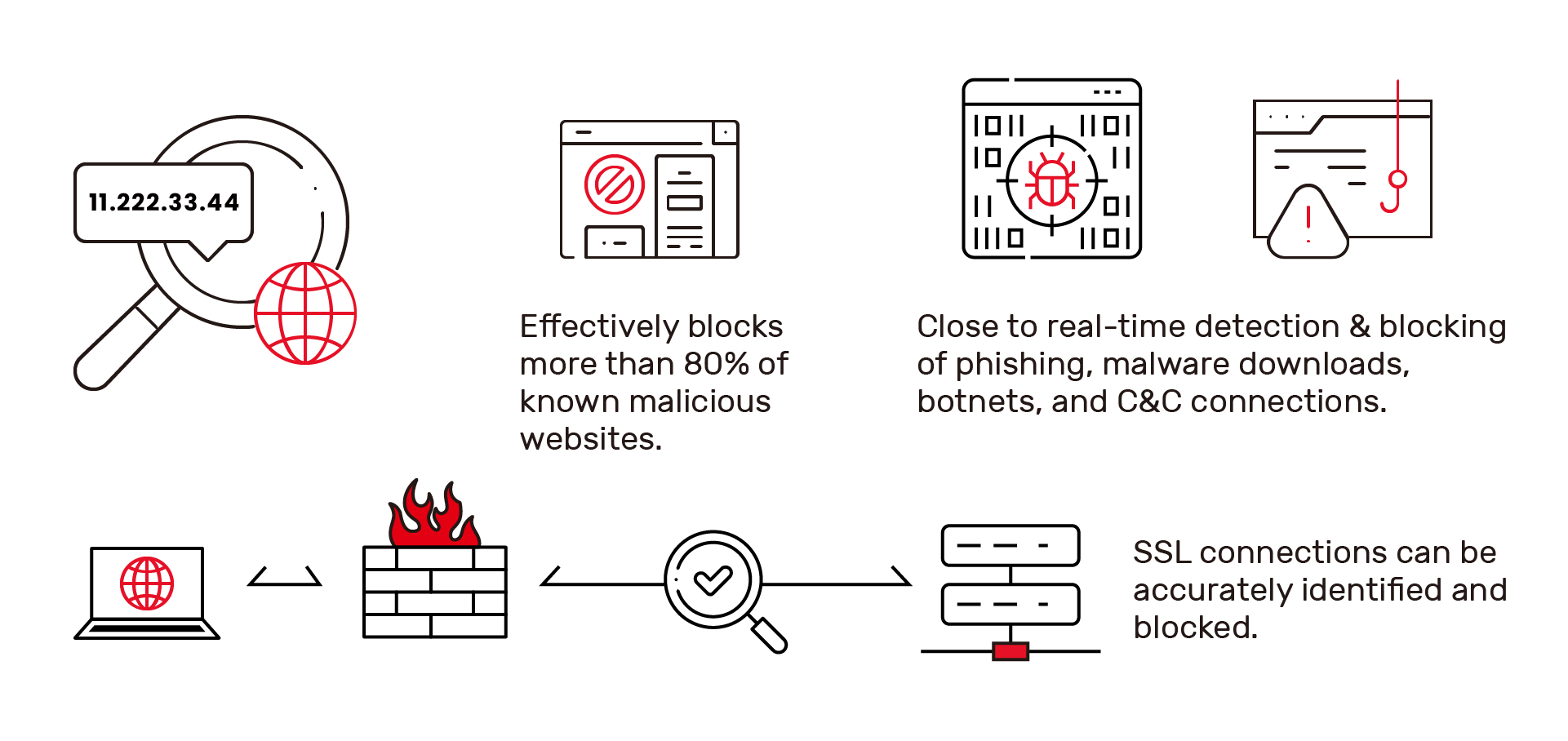 |
Precise Blocking & Rapid Global Intelligence Updates | 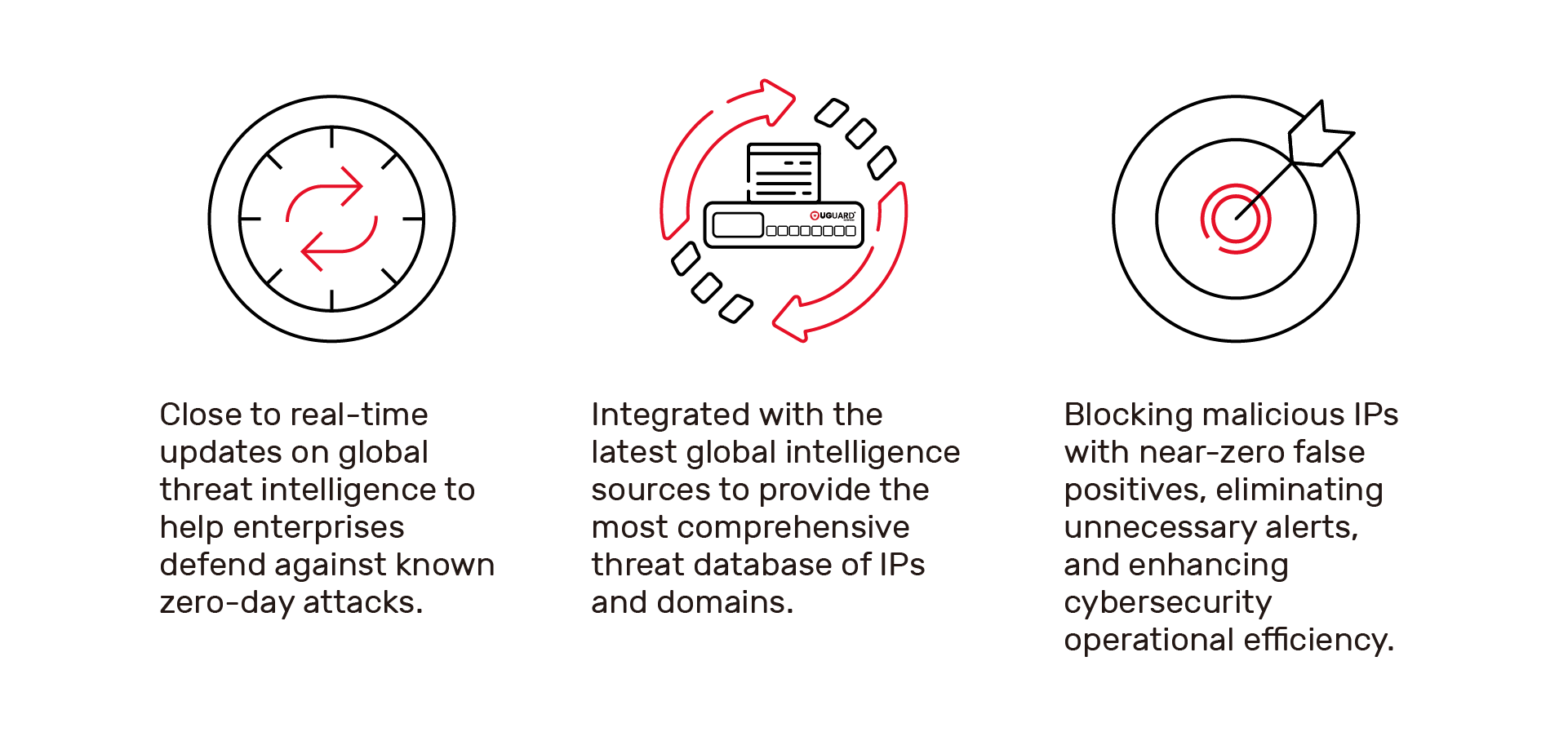 |
Newly Developed With High-Speed Processing PerformanceNewly developed with DPDK(Data Plane Development Kit) to enhance bidirectional forwarding performance. | 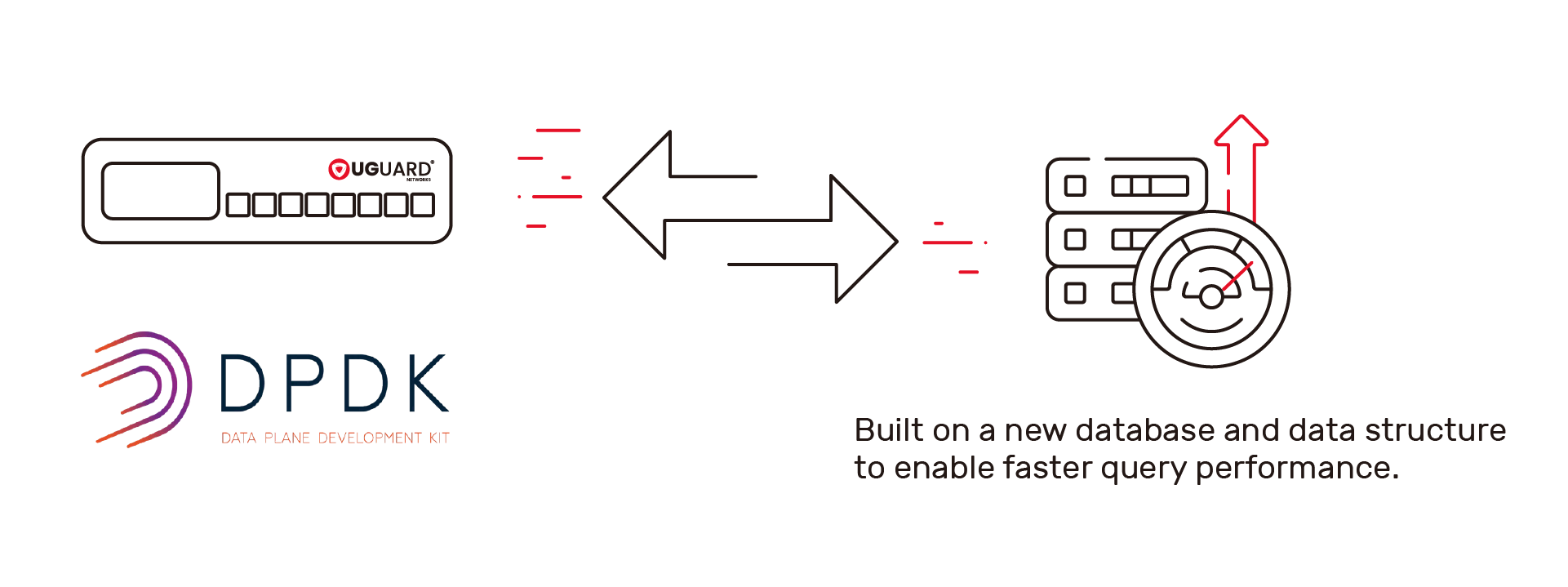 |
Enhanced Security Framework with Optimized NGFW PerformanceDefense Trust can significantly reduce the NGFW security workload, freeing up computing power for more complex security event analysis. | 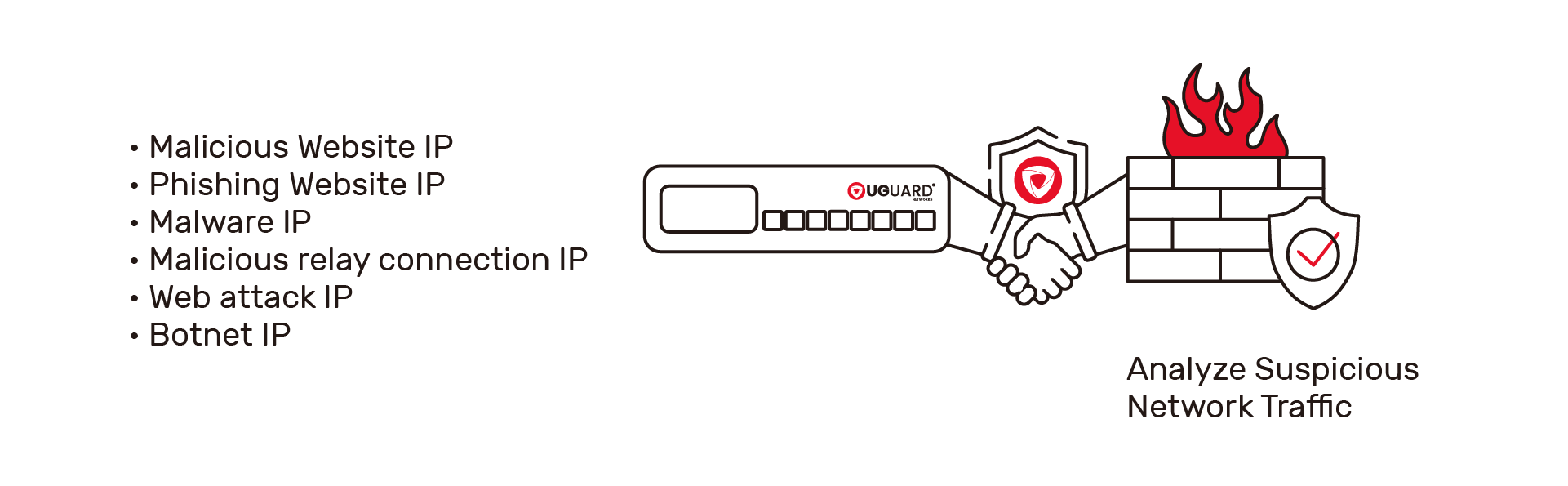 |
Real-time Monitoring for Effective Threat Defense!
|  |
Total Solution for Threat Control and Detection
|  |
Smart Operation, Simple and Easy to Understand!
|  |
 還沒找到最適合的?
還沒找到最適合的?
別擔心,還有更多雲端工具等你探索
IScloud360 集合百款合法 SaaS,從人資到行銷、從財務到客服,總有一款能解決你的問題
前往館別總覽

-
0987654321
Service Hotline
Customer service hours 9:00 - 18:00
-
test111@iscom.com.tw
Contact Email
Send your valuable comments by E-mail
 Continue Shopping
Continue Shopping
 Once your order is complete, we'll send the order details to your email.
Once your order is complete, we'll send the order details to your email.
 Cart Details
Cart Details
 即時線上報價| 免等待立即登入試算
即時線上報價| 免等待立即登入試算
 Request for Quotation
Request for Quotation
