資料處理中, 請稍候...
Loading...

Aqua Security
Aqua Security specializes in protecting containerized applications and microservices, delivering end-to-end security from development to runtime, ensuring workload security and compliance.
Select plan and quantity
Cloud-Native Application Protection Platform (CNAPP) Expert
Accelerate your enterprise transformation, regardless of scale, with tailor-made protection for your cloud-native applications.
Aqua Platform secures workloads whether they are in the cloud, across virtual machines, containers, or serverless environments!
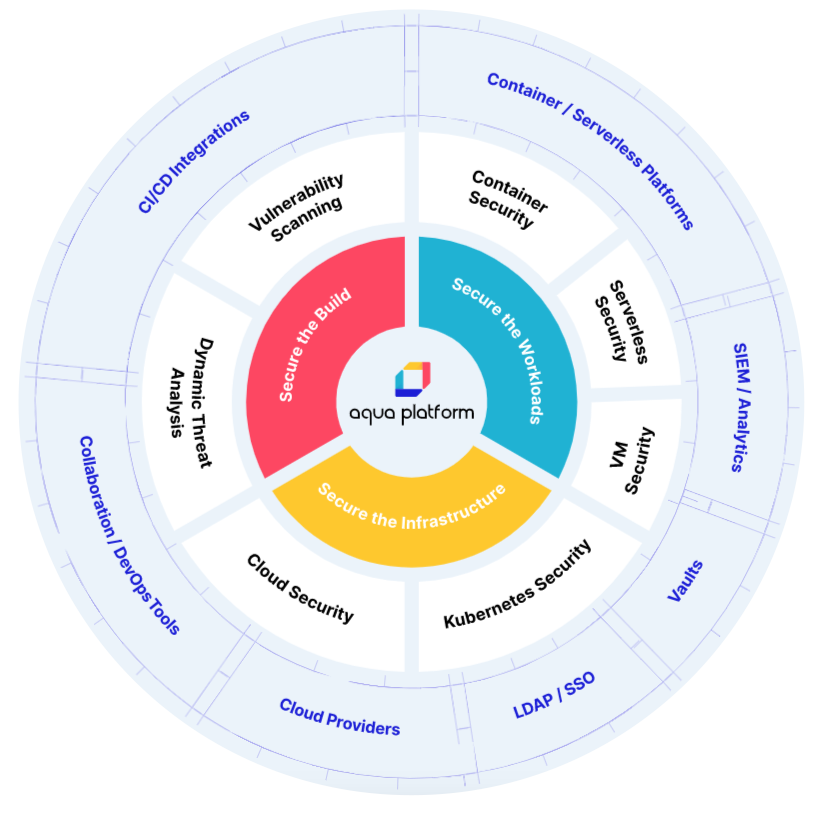 | Comprehensive Kubernetes SecurityLeast Privilege Access for KubernetesMinimize risks from over-provisioned roles and service accounts while reducing dependency on deep Kubernetes security expertise. CIS Kubernetes BenchmarkingAutomatically assess Kubernetes environments against CIS Benchmarks with over 100 individual checks, daily scans, and detailed audit reports. Kubernetes Cluster Penetration TestingRun automated penetration tests on Kubernetes clusters to detect vulnerabilities exploitable by attackers. Firewall RulesEnforce container-level network policies using Aqua’s identity-based firewall. Seamlessly integrates with Kubernetes CNI plugins such as Weave, Calico, Flannel, and Contiv. |
 Build ProtectionShift security left to stop threats and vulnerabilities early, enabling DevOps teams to identify and fix issues rapidly. |  Infrastructure ProtectionAutomate compliance and security posture for public cloud IaaS and Kubernetes infrastructure using best practices. | 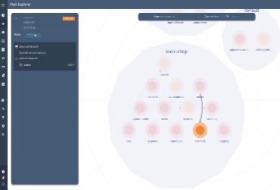 Workload ProtectionSecure VMs, containers, and serverless workloads with fine-grained controls, real-time visibility, detection, and response. |
Risk-Based Vulnerability Management for Container ImagesAqua classifies, filters, and prioritizes vulnerabilities based on continuously updated threat intelligence and runtime context using: CVE Severity & CVSS Scores Exploitability: Whether the vulnerability is exploitable and reachable over a network Exposed Workloads: Whether the workload is affected by the CVE in runtime Running Images: Active workload detection for vulnerable images | 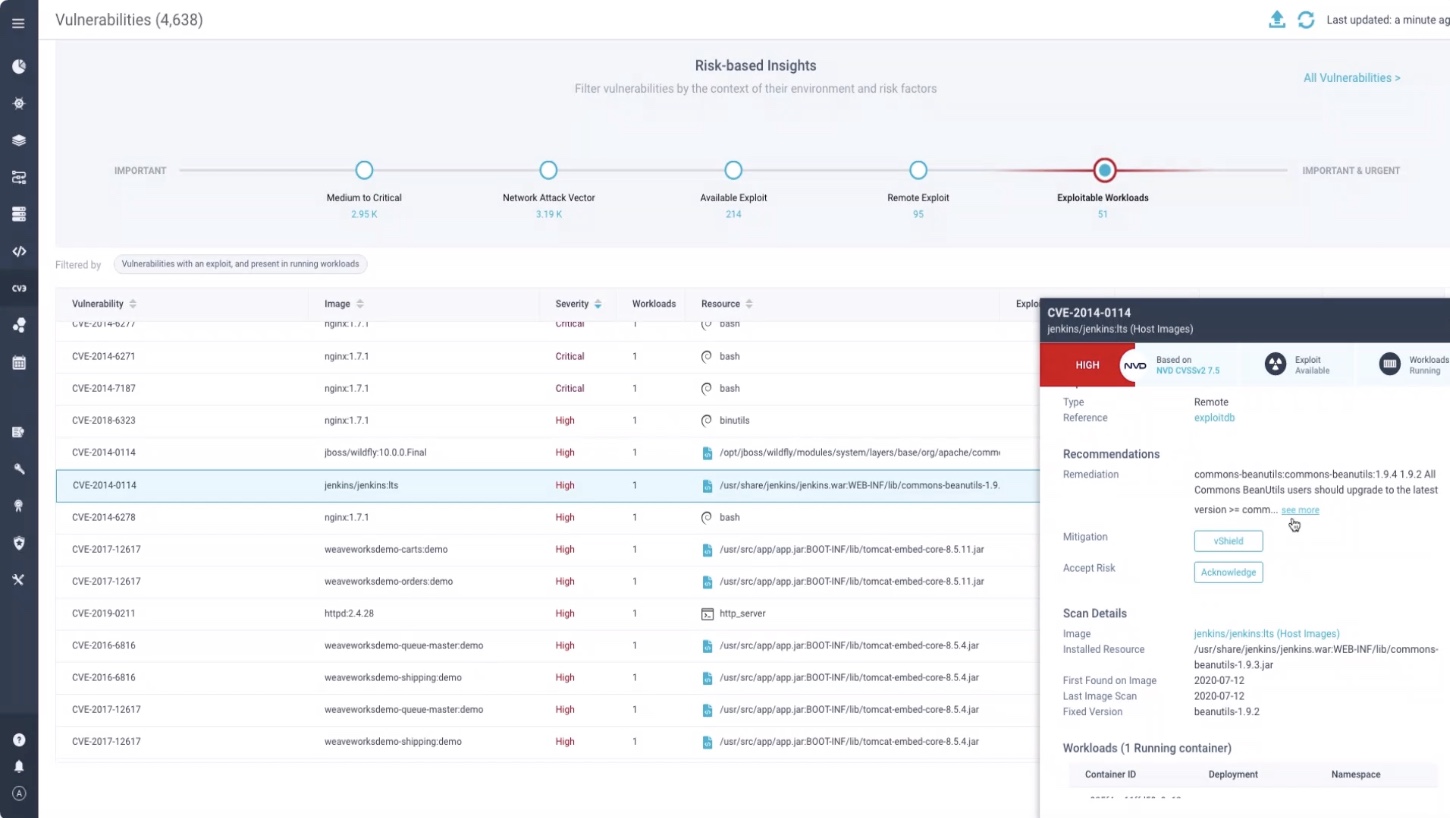 |
CI/CD Pipeline Integration for Automated SecurityAqua CSP integrates into CI/CD pipelines to enforce application delivery security. It flags or blocks policy violations and provides developers with real-time feedback. Supported tools include Jenkins, Azure DevOps, Bamboo, GitLab, and Codefresh. | 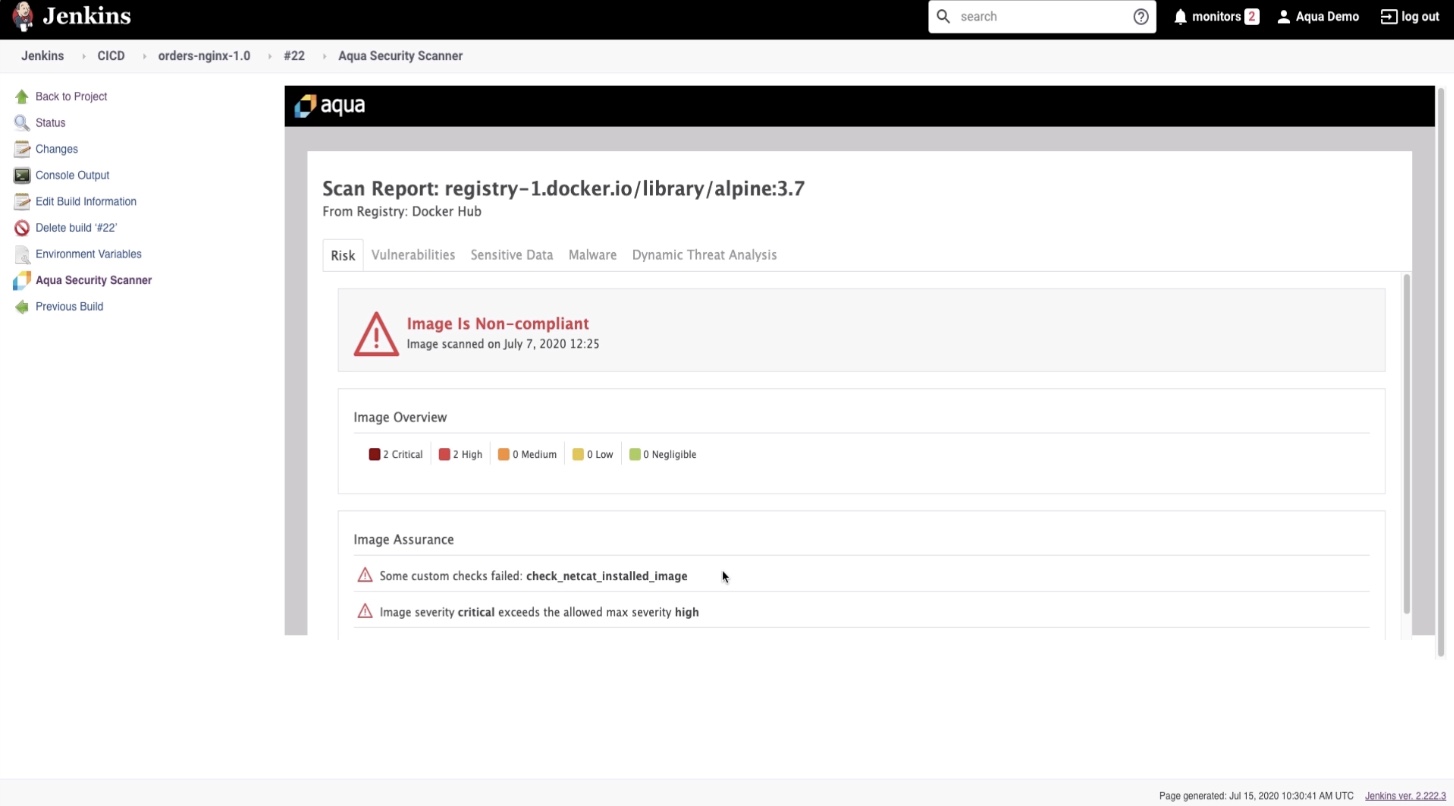 |
Dynamic Threat Analysis (DTA) for ContainersDetect advanced malware hidden in open-source and third-party images that can evade static scanners. Prevent attacks like credential theft, cryptojacking, and data breaches. | 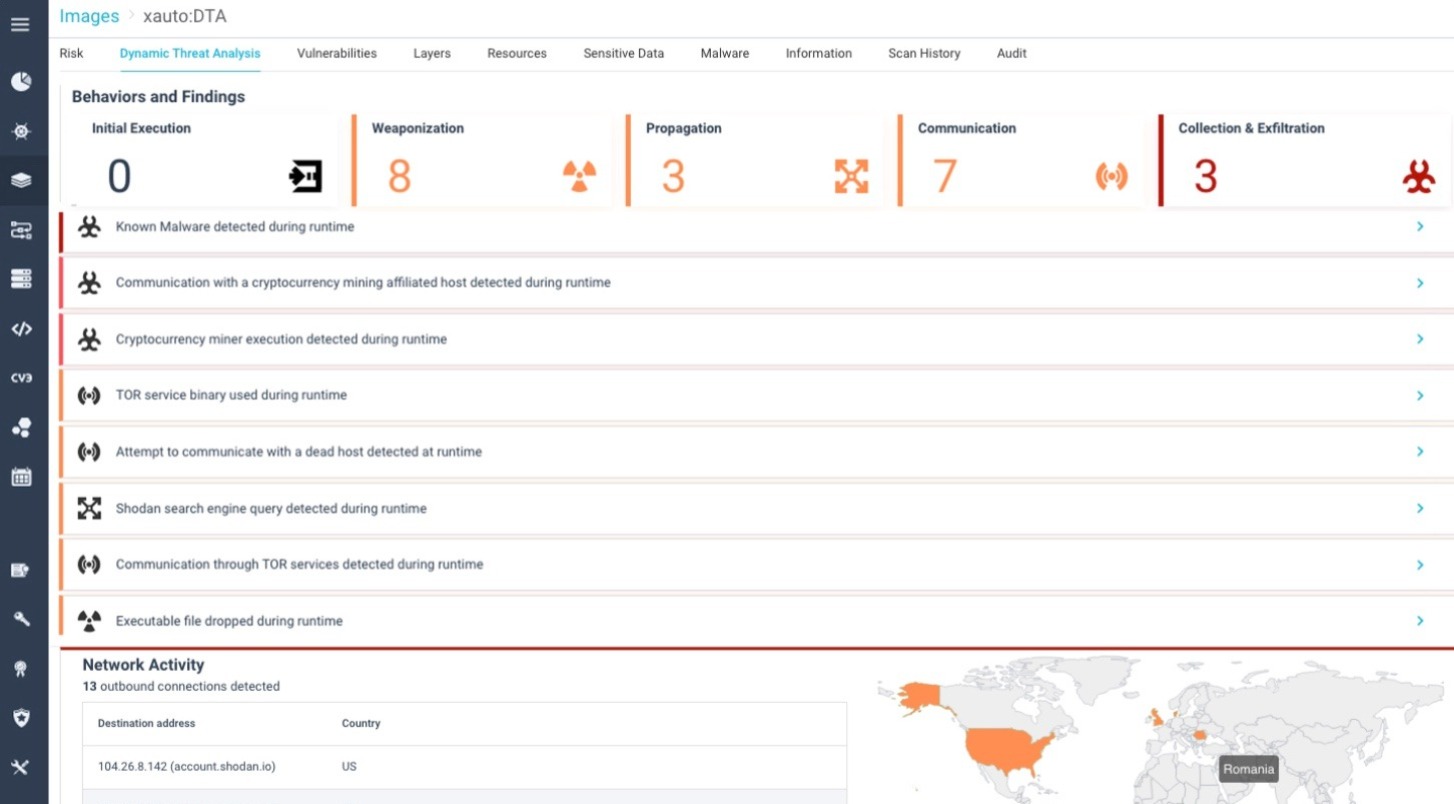 |
Drift Prevention and Runtime Protection for ContainersAqua maintains container immutability and blocks malware from attacking live containers, mitigating attack vectors such as cryptominers, data exfiltration, and zero-day exploits. | 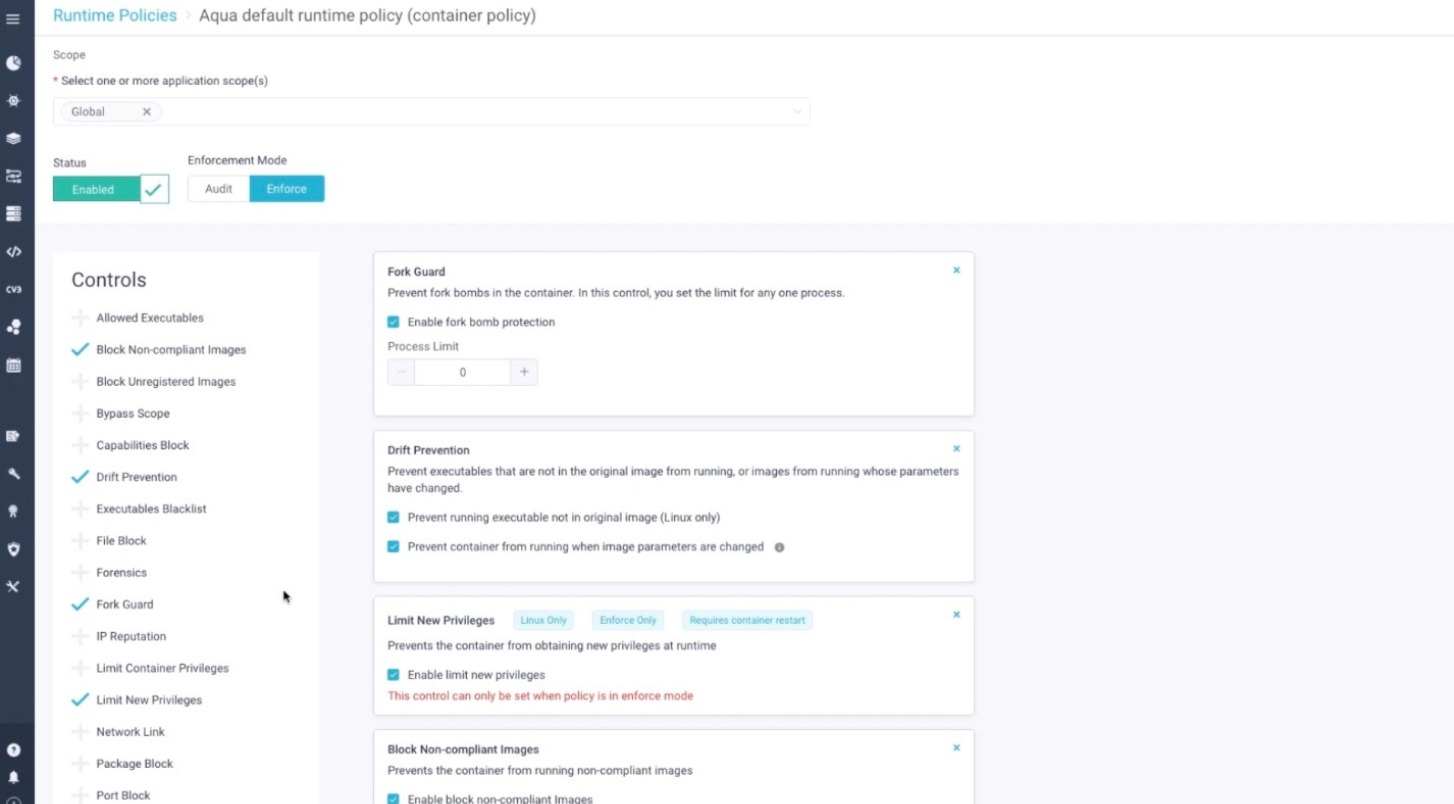 |
Sensitive Configuration & Secrets ProtectionEnforce access controls using trusted identity sources (e.g., Active Directory, LDAP, cloud identity platforms). Authenticate against trusted sources to tightly control access to passwords and encryption keys. | 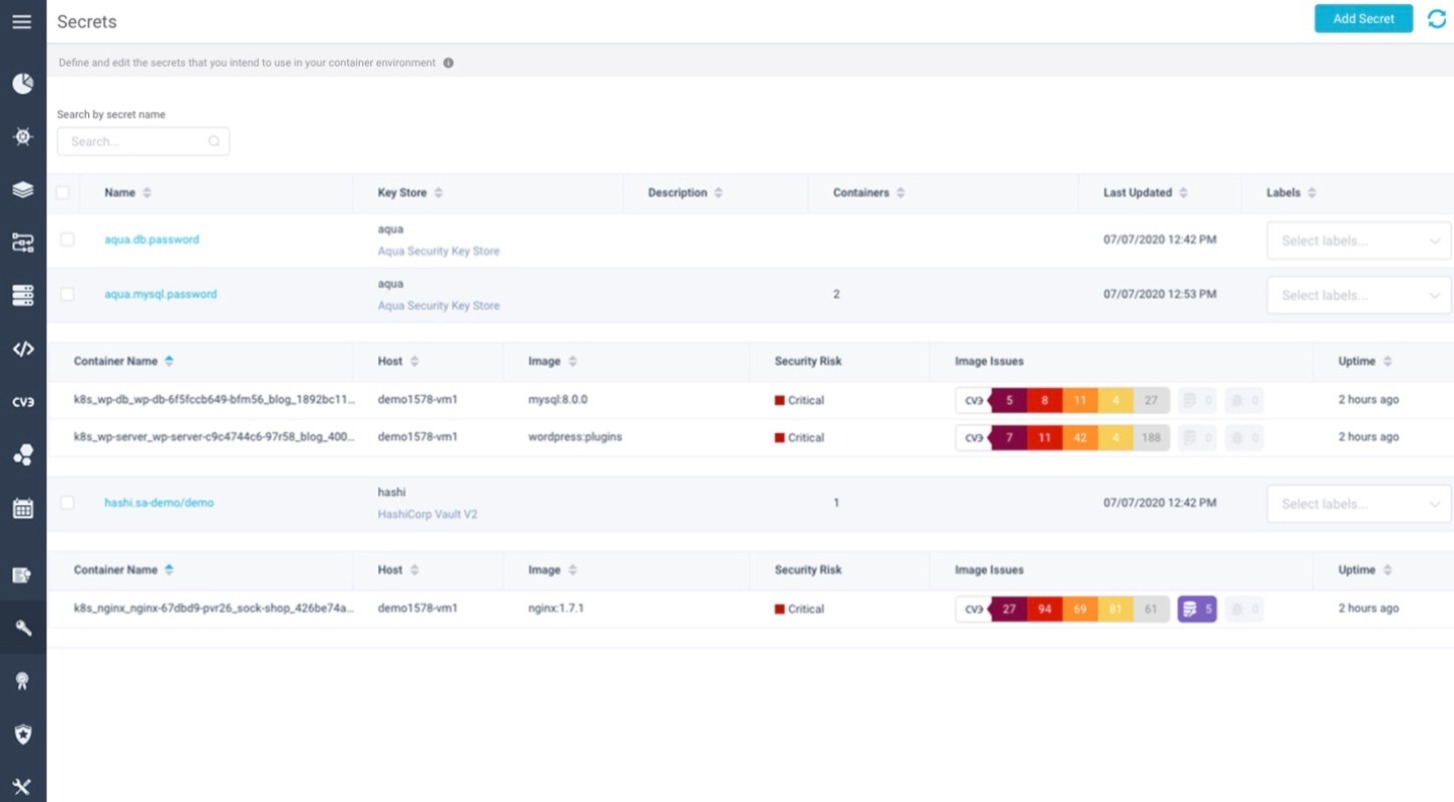 |
Kubernetes Risk VisualizationAqua Risk Explorer provides a visual interface for managing Kubernetes risks, with intuitive prioritization of threats originating from multiple sources. | 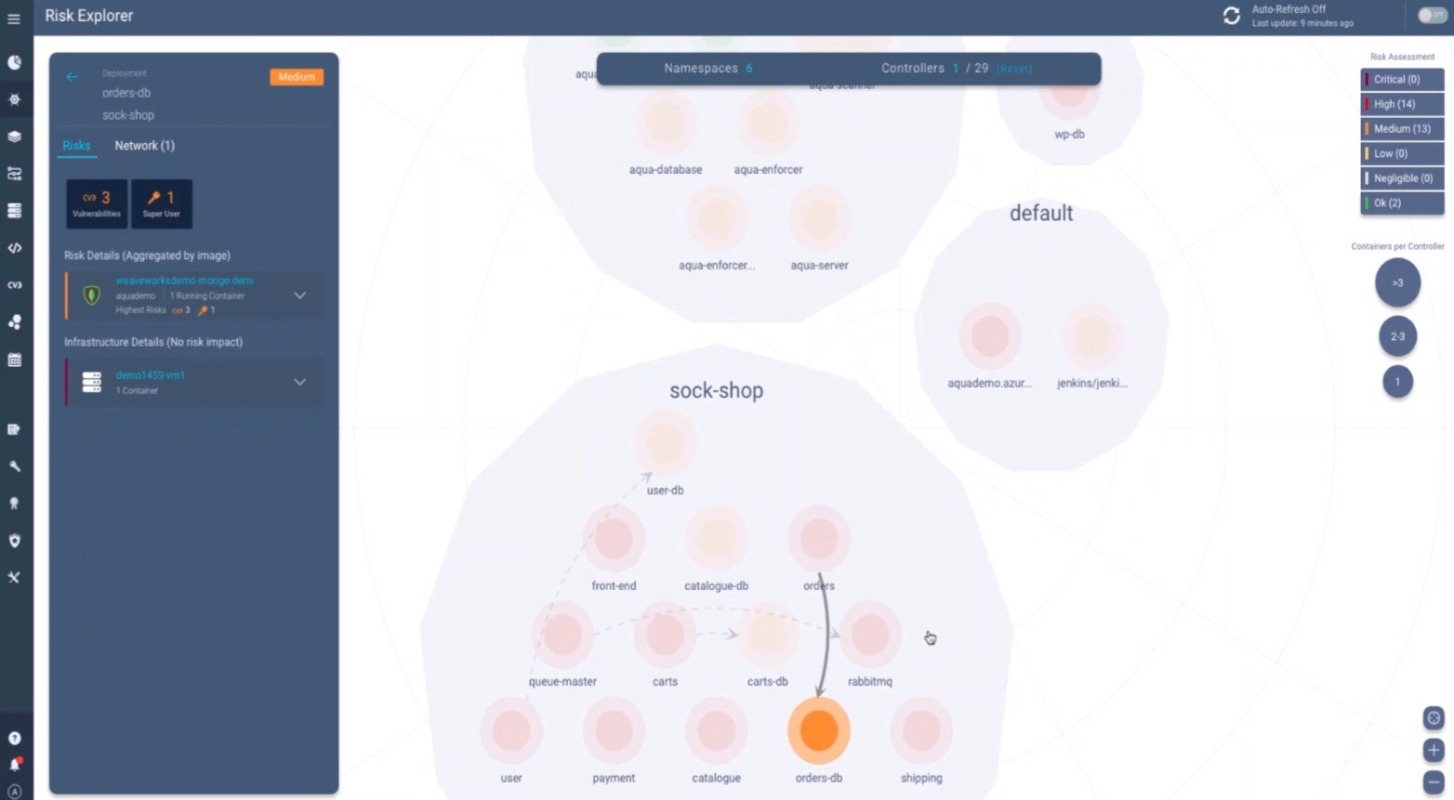 |
 還沒找到最適合的?
還沒找到最適合的?
別擔心,還有更多雲端工具等你探索
IScloud360 集合百款合法 SaaS,從人資到行銷、從財務到客服,總有一款能解決你的問題
前往館別總覽
-
0987654321
Service Hotline
Customer service hours 9:00 - 18:00
-
test111@iscom.com.tw
Contact Email
Send your valuable comments by E-mail
 Continue Shopping
Continue Shopping
 Once your order is complete, we'll send the order details to your email.
Once your order is complete, we'll send the order details to your email.
 Cart Details
Cart Details
 即時線上報價| 免等待立即登入試算
即時線上報價| 免等待立即登入試算
 Request for Quotation
Request for Quotation
